Personal Access Tokens
Personal access tokens grant programmatic access to the Ready Five GraphQL API available using POST requests to https://graphql.readyfive.io/graphql. Each user can create one or more personal access tokens in their account and the access token provided can be used as a permanent authentication token for API requests.
When making requests, set the Authorization header with your token value provided as a bearer token:
POST /graphql HTTP/1.1
Authorization: Bearer r5p_9LZkBKxvaLmSICWkEReIj3QqSiN6V
Content-Type: application/json; charset=utf-8
...
Each personal access token specifies scopes for what it can access. For example, you can grant the incidentsRead scope, which will grant read-only access to incident data. Requests for any other types of data or any attempts to write incident data will be denied. Similarly, granting the teamsWrite scope will allow creating, updating, or deleting team data but will deny all read requests and will deny write requests to any other resource type.
The permissions granted for a user will always take precedence over the scopes defined on the token. For example, if a user is a non-administrator and they create a personal access token with a teamsWrite scope, they cannot create teams, rather they can only write to teams they have permissions to manage.
For all write scopes, users can read the immediate result following the write even if they are not granted the corresponding read scope. Subsequent read requests will be denied.
Create a personal access token
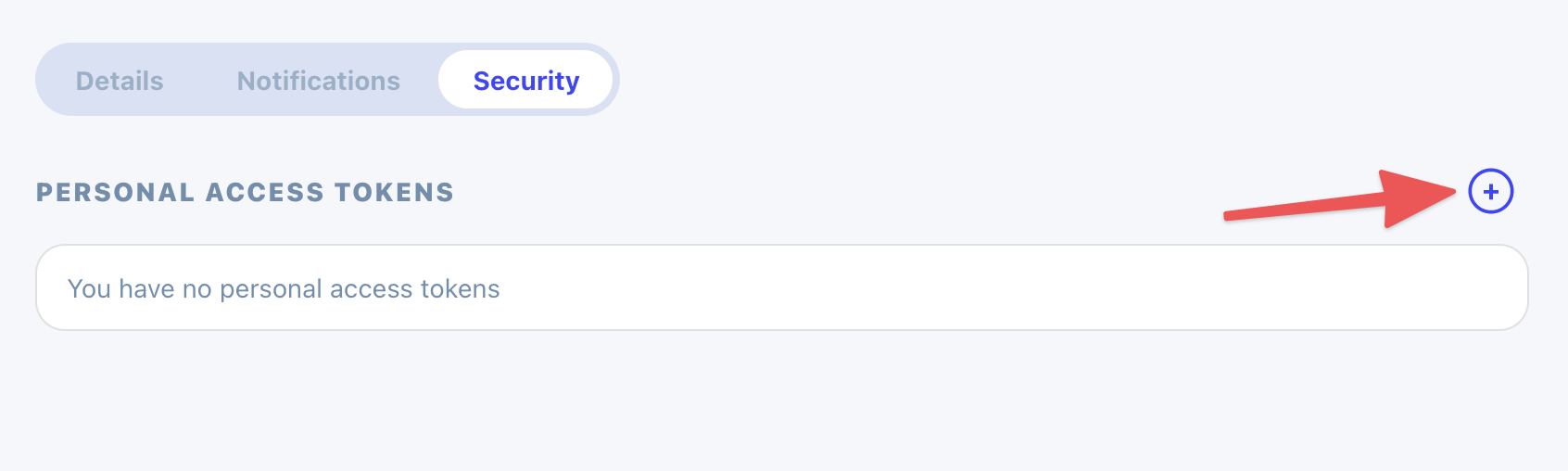
On the profile screen there's a security tab, where each user can create personal access tokens specific to their account. One user cannot see another user's personal access tokens, and their token values should be treated like any password. Never share token values with anyone.
Give the token a description and choose what it will have access to. Each token has explicit read and/or write access to particular resources. Regardless of your selection here, tokens are limited to the permission boundary for the associated user account.
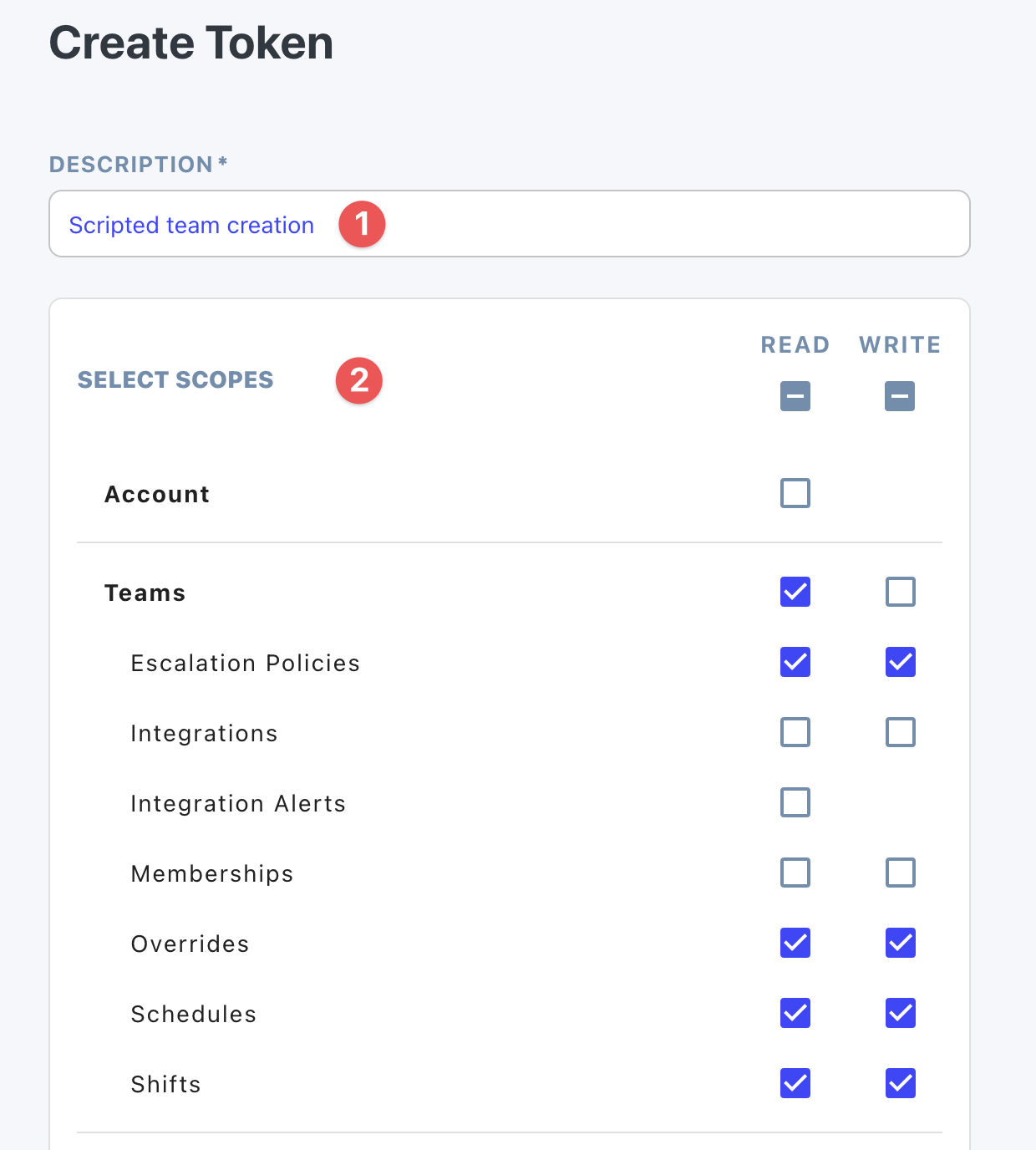
Create the token by tapping the "Create" button.
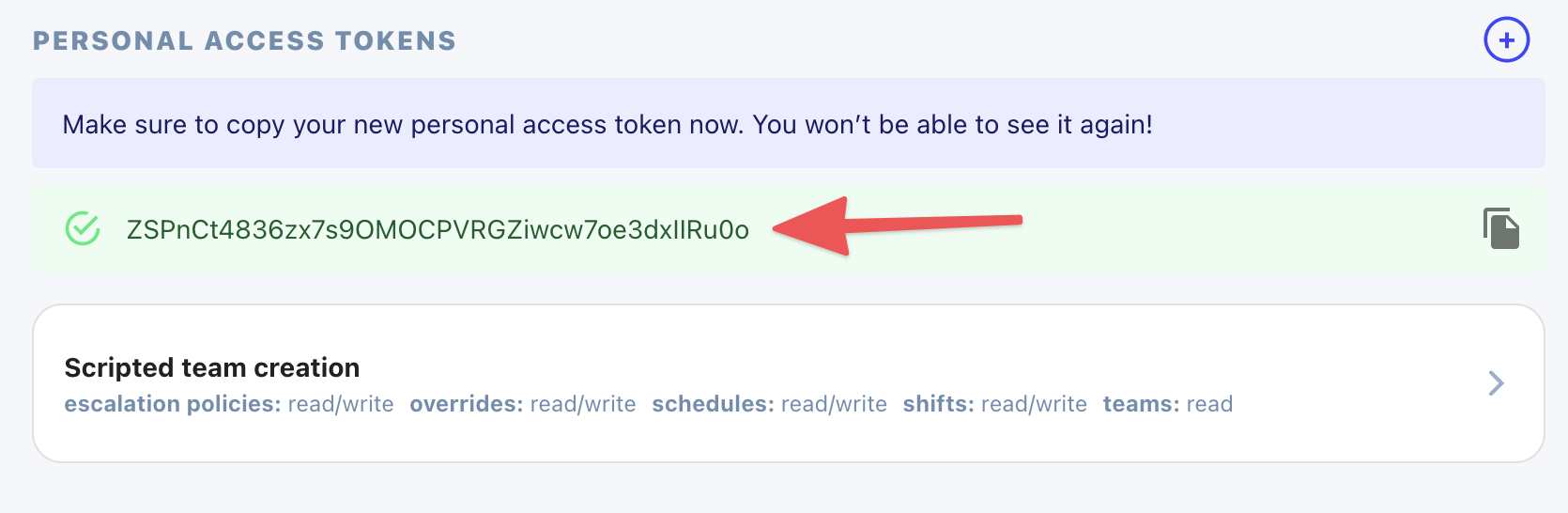
Now that your token was created, copy the token value for future use. You won't be able to see it again and we can't recover it for you! If you lose it, you'll need to generate a new one. And again, never share this token. Consider it equal to a password on your account.
Update personal access token scope
Each access token has zero or more granted permission scopes. These scopes can be changed at any time to expand or limit the token's permissions.
Click the token you'd like to update.
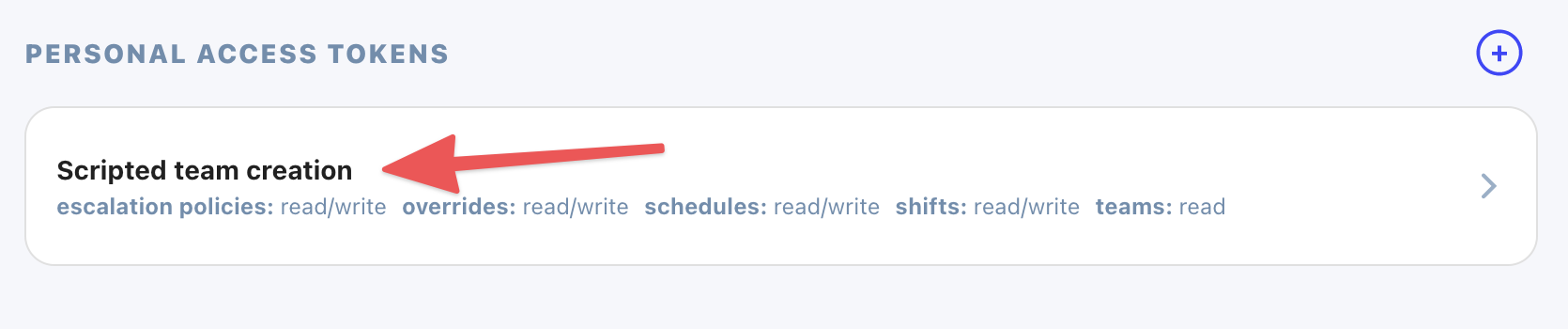
Edit any scopes and click "Update". The new permissions assigned to this token take effect immediately.
Regenerate personal access token
When a new personal access token is created, the user is given its value. This token value is only returned at creation time and can never be requested from the server again. Ready Five does not retain the raw token values, so if a token is lost, it must be regenerated.
Since personal access tokens do not expire, we recommend regenerating tokens periodically as an added security measure.
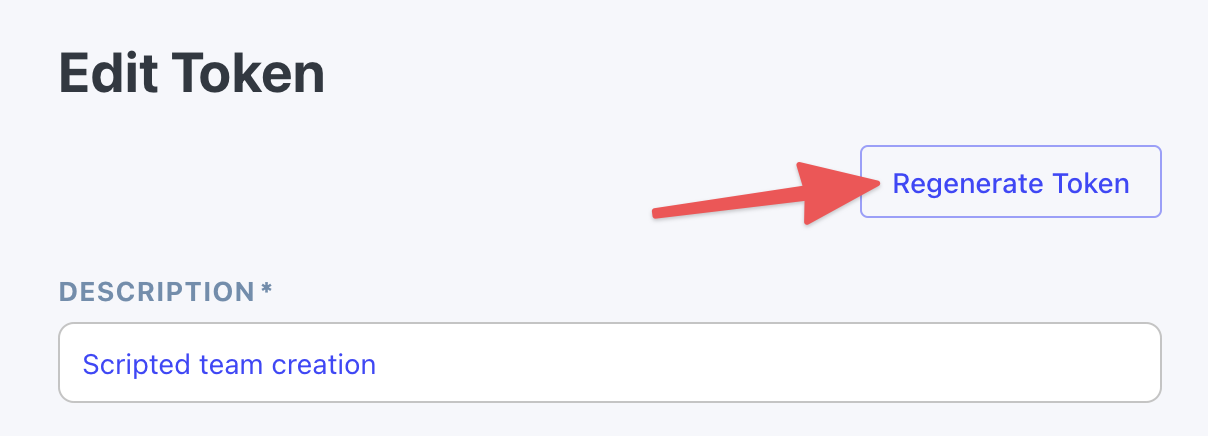
Click the token you'd like to regenerate.

Click the "Regenerate Token" button.
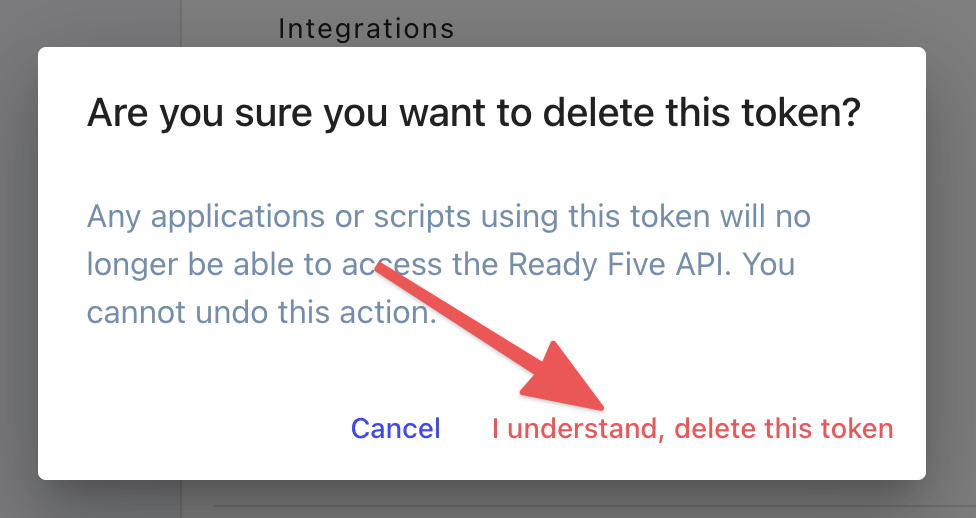
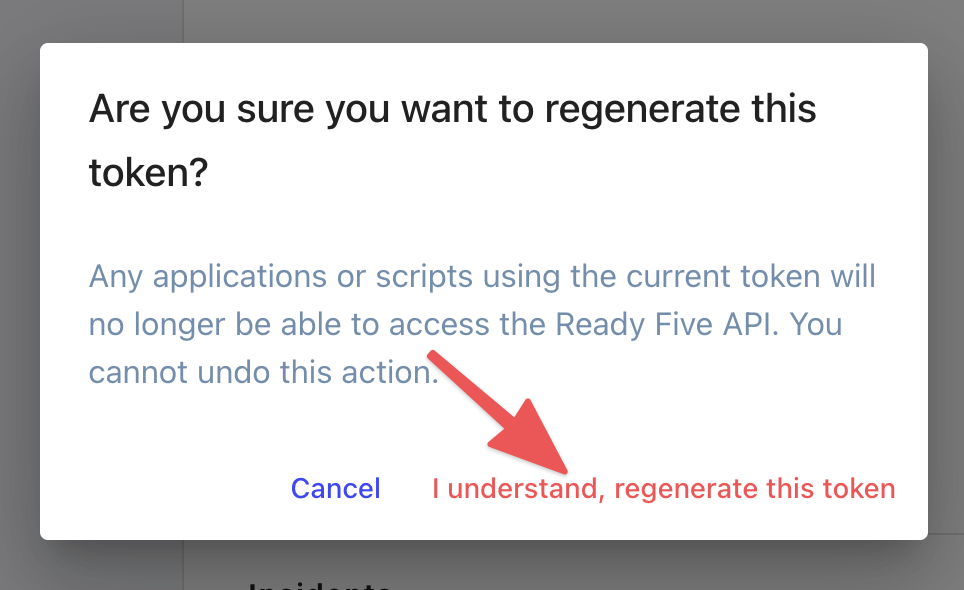
Confirm this is what you want to do.
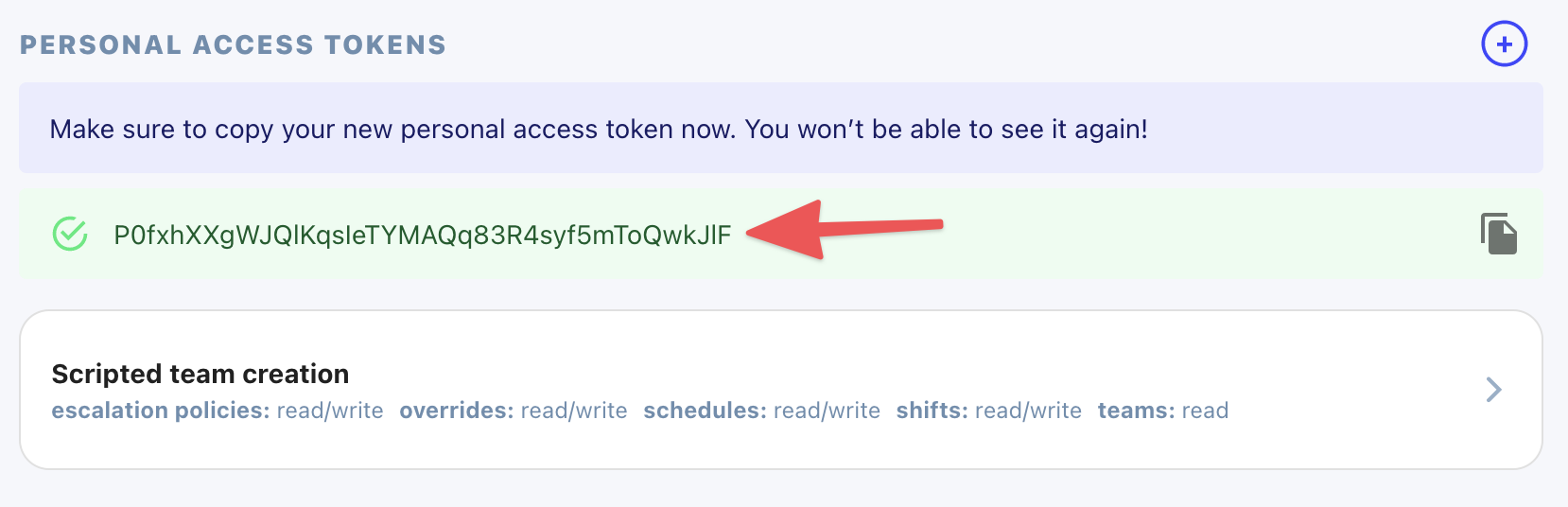
Once again, copy the newly generated token for your use. You won't be able to see it again once you leave this page. The old token is immediately revoked.
Delete a personal access token
If you no longer need a personal access token, delete it to ensure it cannot be used for future requests.
Click the token you'd like to delete.

Scroll to the bottom and click the "Delete" button.
Confirm that you want to delete the token.